Every organization strives to safeguard their highly sensitive corporate information with a robust platform which will help to ensure the integrity and security of their corporate data.Implementing a Information security, cybersecurity and privacy protection management system is one way to ensure that access to data is appropriately authorized and protected. Whatever form the information is in and whatever means it is shared or stored, an information security management system should ensure that data is protected while preserving,
Confidentiality – ensuring appropriate authorization to access information
Integrity – conserving the accuracy and completeness of proprietary information and processing methods
Availability – ensuring access to information for authorized users when required
The goal of an Information security, cybersecurity and privacy protection Management System (ISMS) is to protect the information that differentiates your business, both online and in person. ISMS gives you the freedom to grow, innovate and broaden your customer-base in the knowledge that all your confidential information will remain that way.This is achieved through a system of processes, documents, technology and people that helps to manage, monitor, audit and improve your organization’s information security.
While the implementation of an ISMS will vary from organization to organization, there are certain underlying principles that all ISMS must abide by in order to be effective at protecting an organization’s information assets. The major benefit for an organization in successfully implementing an ISMS is making key stakeholders aware of the need for information security.
The prime benefits of implementing ISMS to your organization are:
It ensures that the organization’s ISMS system is up-to-date on par with changes to the security threats, vulnerabilities and business impacts - an important aspect in such a dynamic field.That’s how ISO/IEC 27001 protects your business, your reputation and adds value.
An ISO 27001 certification can be achieved by any business(e.g. commercial enterprises, government agencies, non-profits) of any size(micro-businesses to huge multinationals), in any given sector(e.g. retail, banking, defense, healthcare, education and government), which is looking to increase and enhance the security of its data.
ISO 27001 isn't an appliance or piece of software that guarantees data breaches won't happen, because such a thing doesn't exist. It is an internationally formalized standard where, your company is required to write and implement procedures based on the actual written standard.The key factors towards an effective ISMS for an organization involves Education, awareness, formalized processes, continual review and improvement, and commitment from all members within the organization.
All organizations, businesses, government groups, academic institutions and nonprofits interested in implementing a framework for the long term protection of their information assets may apply the guidelines and certification requirements of the ISO 27001 standards. Specifically entities may use ISO 27001 to:
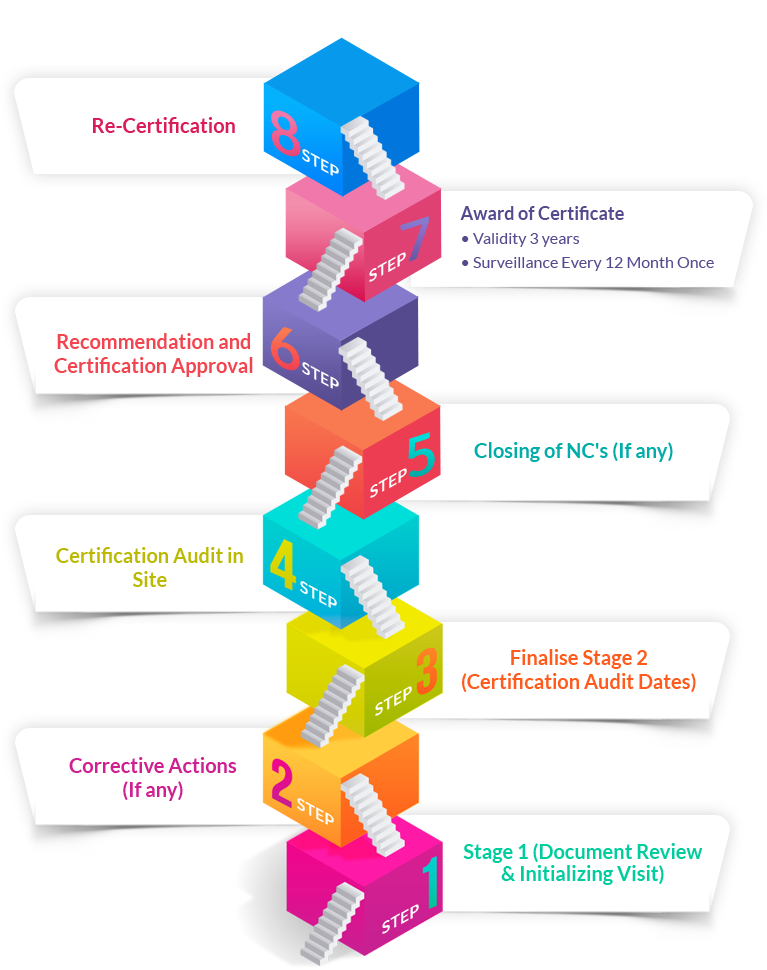
You can transfer the certificate at any stage to us during surveillance/ recertification.
To transfer any certificate IAF has laid down New rules –
So what I need to DO.